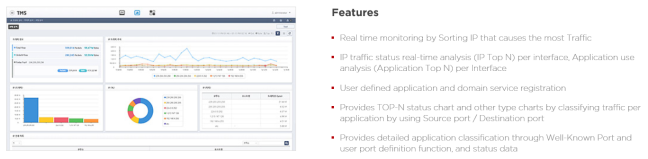
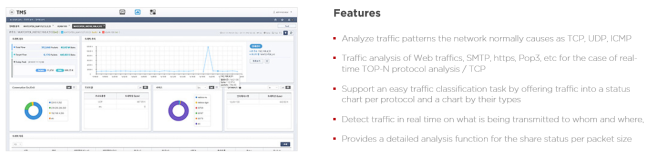
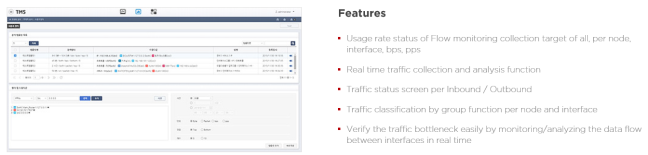
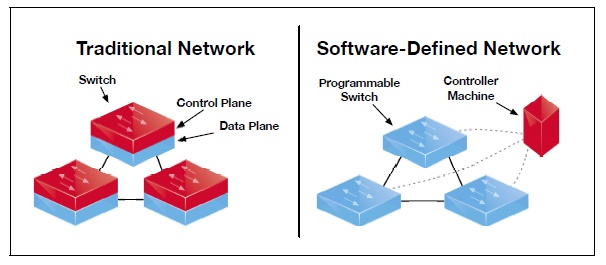
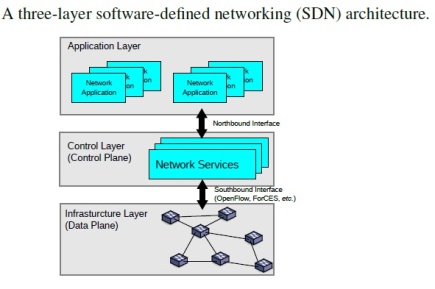
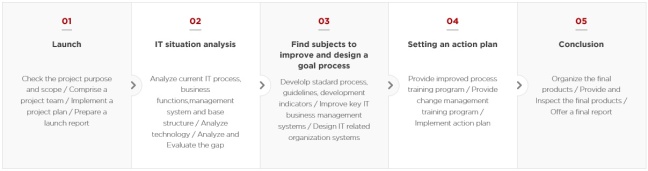
This is information for efficient network management.
1. The nature of the information
The information available for network management generally is incomplete, often incorrect, or intentionally masked or hidden.3 By definition the best one
can expect is that it is statistically representative. The computations performed over the information must not only account for this statistical, incomplete, and large-scale nature,
but must also be selected to match characteristics such as dependence or independence, long-term drift, availability or lack thereof of adequate training sets, and so forth. Generally, the appropriate algorithms are most likely to come from statistical machine learning, but must be selected appropriately to the intended results.
2. Efficiency/performance
As with the measurement, monitoring, and management of information, the tools that comprise network management can themselves also have an impact on the efficiency and performance of the network itself. Algorithms and their implementations must be selected to minimize their impact on performance while providing adequate functionality, accuracy, and detail, but need not provide more than that.
3. Decomposition
In many cases, it will be critically important to be able to decompose and distribute the computations required for a tool or capability. This may be driven by performance or policy constraints on moving information, competition for computing resources, or simply required computational capabilities, such as the limited availability of a particular machine architecture that especially suits a particular functional component. The drivers for decomposition include functionality, geography or topology, and policy.
4. Composition
As with the challenge of sharing and reusing information, it will be important to be able to compose tools or computations into more sophisticated ones. At a basic level, there are and will continue to be a set of tools that do inference over collected data. A simple example is the inference of lost packet rates. In fact, this may be handled by different tools in different places, but being able to compose a tool for aggregating traffic loss over the links of a path that traverses many networks will require the ability to compose not only the inferences of traffic loss based on local packet traces, but also tools for discovering the links that comprise a path.4 For broad network management capabilities to operate usefully and effectively it is important to support composition of functions or tools.
5. Extensibility
Beyond the problem of composition, we must recognize that network management is not static. New tools and capabilities are being designed and implemented all the time. For network management not to stagnate and become out of date, it is necessary that a composed tool be extensible to incorporate newer and more effective supporting tools as they become available. The challenges here include not only how to discover them, but also how to invoke or use them, without requiring human intervention for each new extension.
6. Organizing framework
In order to relieve network managers of the often extremely detailed and complex tasks of organizing network management functions under differing and often changing conditions of physical organization, behavior criteria, and policy constraints, there is a need for a framework that can operate over a set of constraints and objectives to organize network management tools appropriately and then evaluate the effectiveness of that organization. Even the initial structuring,
organizing and location of functionality is not an easy task. There is a significant open question of how to be able to evaluate the effectiveness of a framework set of decisions for organizing network management function. One must ask about a variety of questions such as the nature and source of the evaluation criteria such as what are they, how accurate or flexible can they be, etc. In addition one must ask about the scope and time over which such evaluations might take place.
Resource: MIT Computer Science and Artificial Intelligence Laboratory